Top 10 Web Application Security Best Practices & Flaws with Examples

Web application security is a broad term that encompasses a number of different measures that can be taken to keep the applications you use, and the data they store, secure. This includes everything from patching holes in your operating system, to making sure that the people who have access to your apps are trained and educated in security best practices.
But what does it mean for your app? What are the risks? How do you know if your app is secure? Let’s take a look at what web application security is, how it works, and how it impacts you.
The biggest challenge with web application security is that it takes a lot of work to quantify. You might ask, “Is my site secure? How secure is it?” And there’s no simple way of measuring that. This article gives you the most important things you need to know about web application security, so you can make a good choice for your website.
5 Ways Ignoring Web Application Security can affect your business
1. Security Flaws make your site unavailable, which means no business.
One of the most obvious ways that ignoring web application security can affect your business is that it can make your app unavailable, making it impossible to do business. If an attacker can exploit a flaw in a web application, they might be able to take down the entire server or even the entire cluster of servers that are serving the application.
This could be done through a DDoS attack (distributed denial-of-service) or by compromising machines within the network and using them to launch DDoS attacks themselves. This can result in downtime for your site or service for days or weeks, potentially costing you thousands of dollars in lost revenue!
For example, let’s say you have an e-commerce website that sells clothes. Suppose someone exploits a vulnerability in your site and gains access to customer information. In that case, they could use it to steal money from those customers’ accounts or, even worse, to impersonate them and make fraudulent purchases with their credit cards.
2. Cost in resources & loss of business.
When a company does not have web application security, it can cost them money and business. Web application security is there to protect your information from being breached. A breach of the information could result in financial Loss or Loss of customers.
For example, if someone hacks into your database and steals all of your customers’ credit card information, and sells it on the dark web, then you will have to pay those charges back, which could mean millions of dollars in damages.
Suppose someone hacked into your website’s source code and altered it in a way that resembled but differed from its original design. When people click on something, they think it will take them somewhere else, but it takes them somewhere else entirely. For example, another website that this hacker group compromised also takes them there (which happens more often than you think.)
This could confuse users who are trying to navigate their way through your site or, even worse, make them think there’s something wrong with their computer, which causes them not only stress but also costs you money because now you have people calling you up asking for help which costs you both time and money.
3. Damage to reputation & credibility
When your business has a security breach, you will likely be the first to find out about it. You will also be the one who has to deal with the consequences of that breach—and those consequences can be enormous. For example, if you fail to take appropriate precautions against attacks on your website, you may experience a loss of credibility and reputation with customers.
If someone hacks your website and takes customer data or other sensitive information, customers will be less likely to trust you. This could lead them to stay away from your site or even tell others not to do business with you. In fact, according to the Ponemon Institute, an organization dedicated to research into privacy and data protection, a data breach can cost companies up to $7 million.
That’s not just money lost; that’s time wasted and resources used up dealing with issues from customers, regulators, law enforcement officers, and more. And if you think that sounds bad… well… it is! The Ponemon Institute found that for every dollar spent on protecting data from security breaches, organizations could save $14 in losses due to lawsuits or other legal costs related to those breaches.
4. Legal liabilities, penalties & lawsuits
If you’re not taking web application security seriously, your company is at risk of legal liability. The law requires companies to protect consumer data. You could be liable for any damages if you’ve been negligent in protecting that data. When a company is negligent, severe penalties can follow: fines, lawsuits, and even imprisonment of some employees.
The law is always changing, but here are some examples of what you could be up against:
A. Loss of Intellectual Property Rights
B. Negligence
C. Defamation/Libel/Slander (including online)
D. Invasion of Privacy (including online)
It’s also important to note that if a hacker gains access to your system, they may be able to steal important personal information about your customers, such as credit card numbers or social security numbers. This information could be sold on the black market or used for identity theft purposes—and this is something that you would legally be responsible for!
For example, if you’re running an e-commerce platform and someone uses your site to commit fraud or theft, you could be liable for their actions. In addition to any fines or penalties levied against you by law enforcement agencies, there is also the potential for civil lawsuits from victims harmed by these actions.
5. Data leakage
Data leakage is the accidental release of sensitive information through the internet. This can happen when a website or app fails to protect your details or is not configured properly. Data leakage can be difficult to detect, but it can seriously affect your business.
For example, suppose your customers’ credit card information is leaking. In that case, they may cancel their accounts with you and take their business elsewhere. In other cases, it might be personal information like email addresses and phone numbers being leaked—which could result in new security issues like phishing scams.
You can prevent data leakage by training your staff regularly and using security tools such as firewalls, anti-virus software, encryption software, etc… Despite their initial cost, these tools will pay for themselves many times over by preventing breaches and preventing lawsuits related to data theft.
10 Best Practices for Web application security
Security is an ever-increasing concern for application developers and an often overlooked aspect of application design. Every good developer knows that the most important security measure they can take is keeping source code well-protected. But how do you protect your source code? In this article, you will learn 10 security measures that you can use to reinforce application security in your company’s web applications.
1. Use a web application firewall
A web application firewall is a network security system that protects web applications from attacks by helping to detect and block malicious traffic. A web application firewall can be used to protect a single web application or an entire network of web applications.
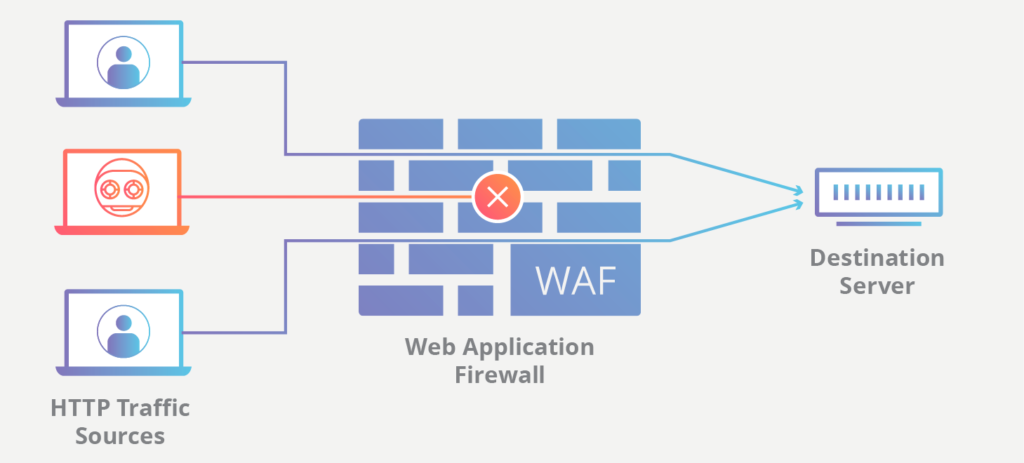
A professional web application firewall should be able to effectively shield your site from various attacks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. It should also come with other security features, such as proactive bot detection and IP reputation management.
2. Keep track of APIs
When it comes to web application security, one of the most important things you can do is keep track of your application’s APIs. This will help you know if someone has used an API for malicious purposes and make it easier for you to identify any vulnerabilities in those APIs.
It’s also important to keep track of when an API is updated by its developers. You never know when a new version might introduce a vulnerability in your application, so you must be informed about these updates as soon as possible.
3. Control access to APIs
The most important part of securing your web application is to control who has access to your application’s APIs. These include any third-party services, such as Google Analytics, which collects data about your users, or databases like MongoDB that store information.
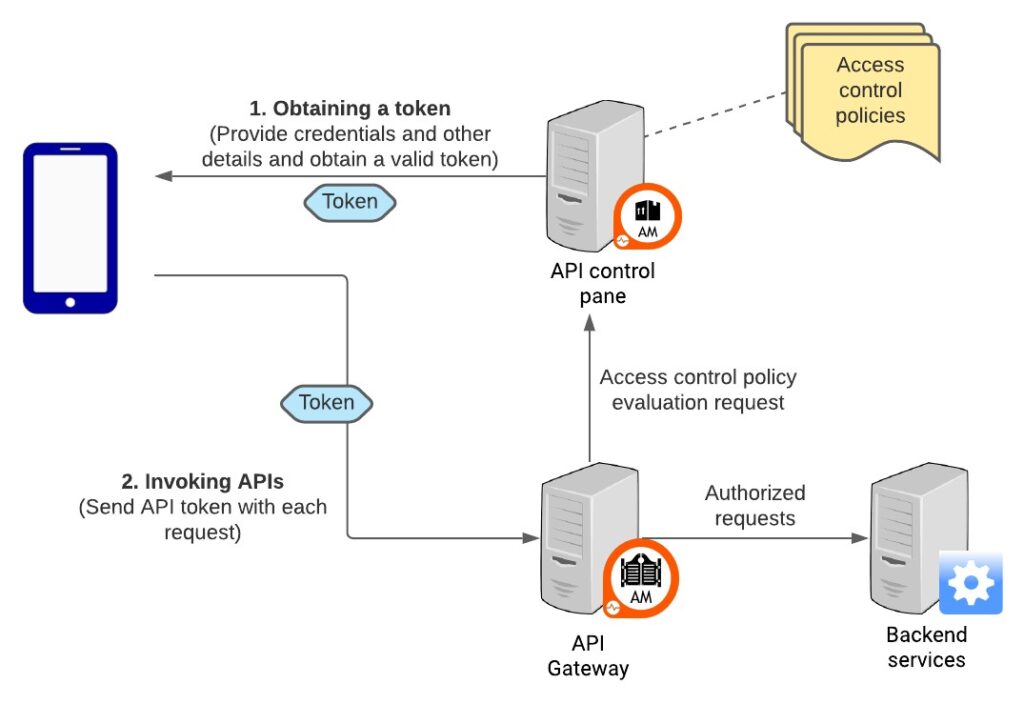
An Overview on API Security
The best way to control access is to use an API gateway. An API gateway allows you to set up rules for who can access what data and when they can do it. For example, you should only allow read-only access from certain IP addresses during off-peak hours or allow only certain users permission to update records in a database.
4. Enforce expected application behaviors
Enforcing expected application behaviors is the best way to prevent attacks.
The most common application security attack is a SQL Injection attack, where hackers try to insert code into an application to access its data. To prevent this kind of attack, you need to verify that any user input is, in fact, what you expect it to be.
For example, if you have a username field on your website that accepts only letters and numbers, don’t just check for those characters; also check for spaces between them so that hackers can’t trick you into letting them enter multiple characters like “John” instead of just “John.”
5. Follow the OWASP Top 10
The Open Web Application Security Project (OWASP) is an open community dedicated to enabling organizations to develop, secure, and maintain applications that can be trusted. The OWASP Top 10 is an industry-accepted list of the most critical web application security risks.
The OWASP Top 10 contains a set of related items frequently targeted by attackers. These items are not limited to “injection” or “cross-site scripting” problems but include all OWASP Top 10 web application threats.
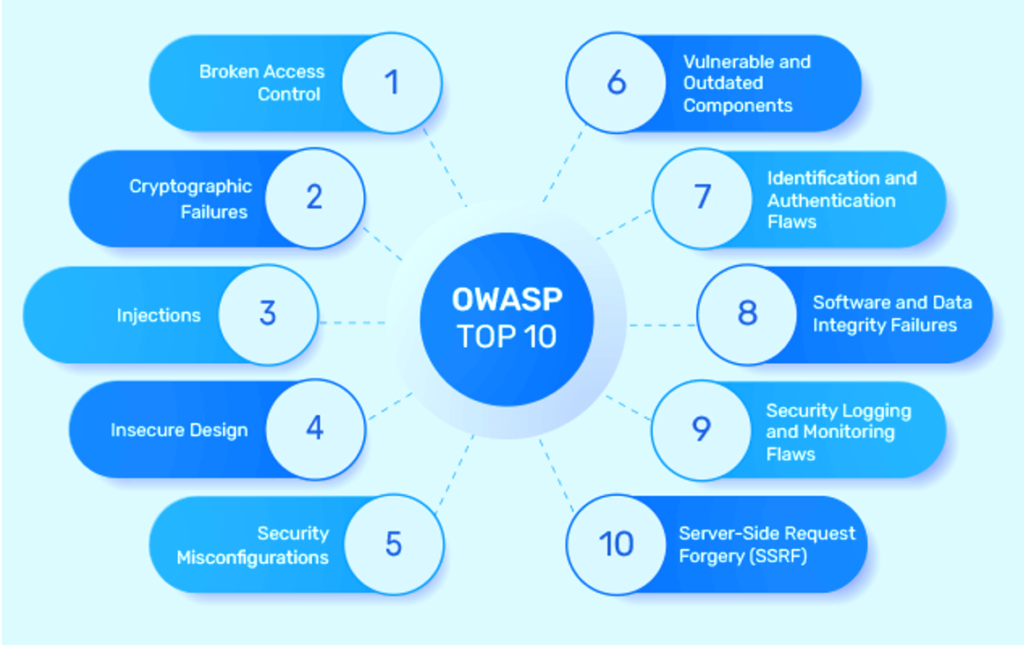
Each item in the OWASP Top 10 has a description of how you can minimize risk and references to other useful materials.
6. Use existing tools and standards
When building a new application, it’s important to use existing tools and standards.
The tools you use in your development process should be able to work with the tools that are already being used by other projects within the company. This way, you won’t have to make major changes to existing processes.
If you’re building something that will interact with other systems, make sure it uses standards already used by those systems. This will help ensure that your code will be compatible with them in the future.
7. Update dependencies
Make sure that you are keeping your web application dependencies up-to-date.
This is especially important if the dependency has been found to have a security vulnerability, but it is also important for other reasons.
If you don’t keep your dependencies updated, then you are running the risk of having a security vulnerability in your application that could lead to data theft, loss of money, or even worse consequences.
It’s best practice to use tools to ensure that your dependencies are up-to-date and secure.
It’s important to know that your web application is secure. One of the best ways to do this is by checking that security is configured correctly.
The first step in configuring your site’s security is determining what vulnerabilities you might encounter. You can do this by learning about common types of attacks, how they work, and which parts of your site are most vulnerable. Once you’ve done this, you’ll be able to identify where your site may be vulnerable and take steps to protect it from attack.
You should also ensure that all users on your site have unique passwords and that they’re not shared between multiple accounts or systems. This will help prevent hackers from gaining access to more than one account at a time.
Finally, ensure that you have a way for users to report issues with their accounts or other problems on your site so that you can address them quickly before they become bigger problems.
8. Set up DevSecOps
DevSecOps is setting up a security team that works with developers to create more secure web applications.
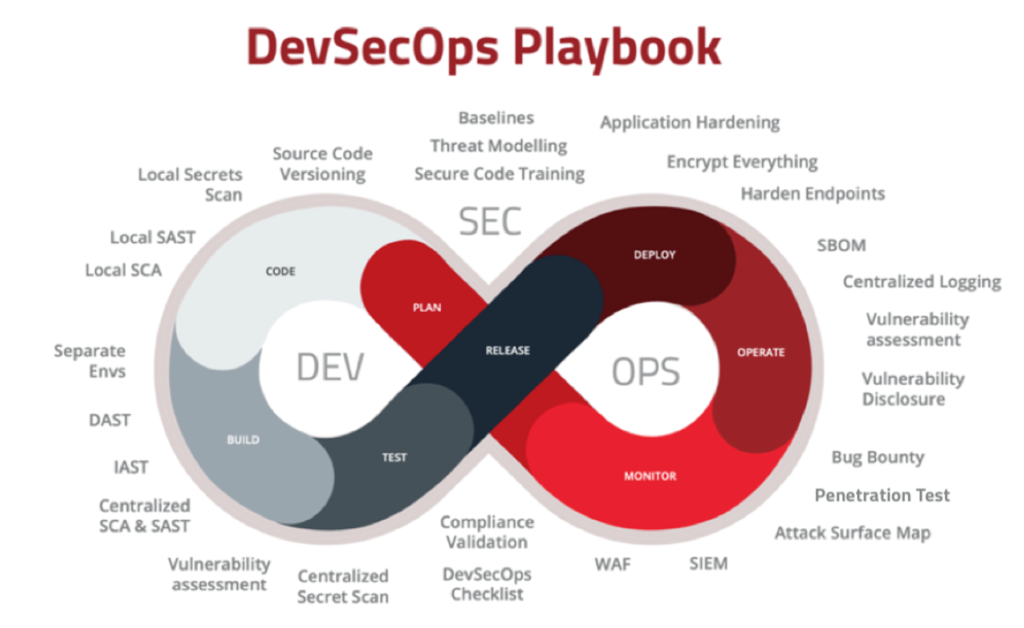
In a DevSecOps environment, developers and security teams work together to find and fix vulnerabilities before they can be exploited. The goal is to prevent any data breach or other security incidents from occurring.
This approach has been shown to reduce the number of bugs discovered after an application has been released and how long it takes for these bugs to be fixed once they are found.
9. Use password managers
As a web app developer, you’re probably familiar with the importance of using secure passwords. But did you know that password managers are one of the most effective ways to ensure that your company’s accounts aren’t compromised?
A good password manager allows you to create unique passwords for every site and manage them all from one place. You can also use these tools to generate strong passwords and automate how often you change them.
The best part about using a password manager is that it makes it easy for your employees to adopt strong authentication practices without requiring much time or effort. As a bonus, they won’t have to remember dozens of different passwords!
10. Stay educated on security changes
If you want to stay up-to-date with the latest in web application security, you’ll need to stay educated.
You can do this by reading articles and blog posts about security issues currently affecting web applications. You can also read about any new vulnerabilities or exploits discovered recently.
Staying educated is one of the best ways to ensure that your company does everything possible to keep your customers safe from online threats.
Top 10 Web Application Security Flaws with Examples
1. SQL Injection
SQL Injection is the most widespread web application vulnerability. It allows an attacker to execute SQL statements on a database and cause damage to a database or data.
A SQL Injection attack occurs when malicious input is supplied to an application to manipulate the underlying database layer in such a way that it causes unexpected behavior for the developer. This could be as simple as providing a username whose name contains ‘OR’ (which would cause the query to return true if both conditions are met) or as complex as altering the structure of an entire SQL statement with quotes around certain values.
For example, if you were building a website that required users to enter their first and last names, and you wanted to keep track of how many users submitted their information, you might create a form that looks like this:
This code would display two text boxes where users could enter their first and last names, but it would also store those values in variables that could be used in other parts of your script.
If someone enters malicious input into either text box (like “OR ‘1’=’1”), it could cause your script to run commands or delete data from the database.
2. Broken Authentication and Session Management
One of the most common Web application security flaws is broken authentication and session management. It’s also one of the easiest to fix.
In a nutshell, broken authentication means that when a user logs in, they can’t be sure they’re logged in as themselves (and not someone else). And broken session management means that once a user has logged in, an attacker can hijack their session.
It’s important to remember that when it comes to authentication and session management, security isn’t just about ensuring that you have a secure login process—it’s also about making sure that your users know what’s going on with their sessions at all times.
For example, if someone steals your cookie and then uses it to log into your account, they’ll be able to access your personal information, including credit card numbers and other sensitive data.
If this problem is unchecked, it could lead to a major breach of privacy.
3. Cross-site scripting (XSS)
Cross-site scripting (XSS) is the most common web application security flaw; it’s a vulnerability that allows attackers to inject malicious code into your application, which users can execute.
The malicious code can be used for various purposes, such as stealing user credentials, session cookies, or other sensitive data. You should update your applications regularly to continue working when new operating system versions come out.
An XSS attack usually occurs when you neglect to filter user input or escape output. It can also happen if you fail to encode special characters in HTML tags before outputting them to the browser. This could lead an attacker to inject malicious code into your website or application.
Common examples of XSS include spam emails, social engineering scams, and fake login pages that trick users into giving up their credentials.
4. Insecure Direct Object References
Insecure direct object references are a major security flaw that can lead to a data breach. These flaws occur when applications accept sensitive data without verifying or cleansing it. This allows an attacker to use the data unexpectedly, even though the application developer’s intention was not malicious.
The most common way for this to happen is through Insecure Direct Object References. In these cases, the application stores user-specific data as part of a URL or other parameter.
For example, if a user enters their credit card number into your application form and submits it, the server will store that information. Suppose there is no validation or sanitation of this data before storing it. In that case, it could give an attacker access to the user’s credit card information.
5. Security Misconfiguration
Security misconfiguration is one of the top 10 web application security flaws. The lack of proper configuration can leave your data open to outside access.
Imagine you’re the administrator of a website that allows users to register new accounts. You’ve built out a registration form but haven’t set up any security or restrictions on who can actually register. That means anyone visiting your site could sign up as an account holder without trouble. The same could happen if you have built-in functionality that lets people pay for products or services with their credit cards—but haven’t set up any security measures around credit card transactions, such as encryption or password protection.
A common example is when a company configures its website with weak authentication or encryption settings. It opens itself up to an attack. This can make it easy for hackers to gain access and steal sensitive data from the site. In many cases, the only way to fix this issue is by manually reviewing each setting and ensuring it’s configured correctly.
6. Sensitive Data Exposure
Sensitive data exposure is a security flaw that occurs when sensitive data, such as passwords and credit card numbers, are accidentally made available to people who should not have access to it. This can happen when the owner of the sensitive information gets careless and leaves it in a location where others can find it or when they fail to keep track of where they’ve stored it.
Data leakage is another form of sensitive data exposure. Data leakage happens when an employee or contractor leaves an organization with sensitive information that should not be shared with anyone outside your business or organization. Data leakage can cause serious problems if the person left with this information decides to use it for their gain rather than share it with legitimate parties who need it for business purposes.
For example, if you’re sending an email with sensitive information in it, and the email gets sent to someone who doesn’t need to see it, that’s an example of sensitive data exposure. Sensitive data can also be exposed when poorly coded applications allow malicious users to access or modify sensitive data.
7. Missing Function Level Access Control
This is one of the most common security flaws in web applications, and developers must take steps to protect against it. It refers to the process of granting access to a function that is not necessary for the operation of an application but still gives it an access control policy.
For example, A web application with a login page to authenticate users and then grants them access to certain functions based on their role in the organization. However, other functions may allow users to edit or view data that should not be available. This could allow attackers to use these functions to view sensitive information or modify records without needing credentials from legitimate users.
8. Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is an attack that forces the user to unknowingly perform actions on behalf of the attacker. The attack occurs when a user has an active session with the application, clicks on a link, or opens a request from a malicious website or email.
You can launch the attack using different methods, including image, form, and script tags. Suppose the user’s browser does not have cookies enabled, and the request does not contain any information about the user. In that case, there will be no way for the server to know who is acting. In such cases, CSRF can be an attack vector.
A typical example of a CSRF attack is when a logged-in user visits an external page containing malicious code that performs some action on the user’s behalf, such as transferring funds from their account or changing their email address.
9. Using Components With Known Vulnerabilities
Vulnerabilities are discovered in software regularly. When a vendor discovers the bug, the vendor sends a notice to all other vendors and issues a public announcement. This allows them to fix their code and release an update for their customers. In most cases, developers can use components with known vulnerabilities in their applications, but they should be aware that attackers can exploit these components if they aren’t properly secured.
The most common way to use components with known vulnerabilities is by using a package manager like npm or composer. When you use these package managers, they will fetch the latest version of your dependencies from their respective repositories and install them in your project automatically if you don’t specify otherwise. Since these repositories are public and open source, attackers can easily find exploits that allow them access to your application.
Example: A company is using a third-party component in its web application. The component was tested and deemed secure at some point but was never checked again after that initial test. The company continues to use this component without checking on it now and then. As a result, they end up with an insecure web application due to newly discovered vulnerabilities in the third-party component.
10. Unvalidated Redirects and Forwards
One of the most common web application security flaws is the unvalidated redirect or forward. Redirecting a user to an external URL without validating it results in this error. The attacker could run scripts in your browser to steal your credentials if the target URL is malicious.
This attack can be harmful if you log into a website that uses cookies. An attacker could use JavaScript in their malicious page to modify your cookies and hijack your session with the target website—even if it’s not vulnerable to cross-site scripting (XSS) or SQL injection.
For example, imagine you’re shopping for shoes at Nike’s website, and you add some items to your cart. Your next step might be to log in and check out, but before doing so, you click on a link that takes you to another site where someone sells counterfeit shoes at a lower price than Nike’s official store.
The link redirects you back to nike.com without any validation from Nike itself; therefore, it can’t determine whether the URL is safe before redirecting you there—which means that Nike may not know how many people end up visiting those counterfeit sites!
10 things developers need to know about Web application security
1. SQL injection is still the most common and dangerous Web app vulnerability
SQL injection is still the most common and dangerous Web app vulnerability. It’s not just a problem for developers to be aware of but for users.
In an SQL injection attack, hackers try to manipulate data in a database by entering malicious code into a form or URL parameter on an application. This can lead to loss of data integrity, unauthorized changes to data, or even remote code execution.
Because it’s so easy for attackers to exploit this vulnerability and the consequences can be so damaging, developers must be aware of all possible ways to accidentally introduce SQL injection into their applications.
2. The cloud doesn’t make you more secure
The cloud is not the cure-all many companies believe it to be.
The cloud offers many benefits: It can help you access your data from anywhere and is an excellent way to distribute your software across multiple servers. But when it comes to security, the cloud is just as vulnerable as any other platform.
In fact, in some ways, it might be even more so. Because of its distributed nature, there are more ways for an attacker to get into your system through traditional means like SQL injection or cross-site scripting (XSS). You must ensure that your provider has taken measures to protect against these attacks before you start hosting there.
3. Developers need to use multiple tools for static and dynamic analysis
One of the most important things developers need to know about Web application security is that they should use multiple static and dynamic analysis tools.
When building an application, it’s important to view it from different angles and ensure you’ve thought through all possible scenarios. For example, if you are working on an e-commerce site, you want to make sure that your user’s credit card information is safe while they’re browsing and buying products online.
This can be difficult when relying on just one tool, like a web browser or a development IDE (integrated development environment). That’s why developers should use a combination of tools, such as static analysis tools (which check for vulnerabilities in code) and dynamic analysis tools (which look for vulnerabilities in the runtime environment).
4. Modern Web apps require modern testing tools
Modern Web apps are complex. They require many different technologies to work together, and they’re often hosted in the cloud. That makes them more vulnerable to security threats than traditional desktop software.
Testing tools are essential for ensuring that your application is secure before launch. This article will look at what testing tools are available, how they can help you avoid costly and embarrassing problems later on, and how to pick the right tool for your needs.
Traditional tests don’t cover the full scope of web app security risks. To ensure your app is secure, you need tests that emulate real-world attacks, such as phishing, SQL injections, and cross-site scripting attacks.
5. Security is a process, not a product
It’s easy to think of security as something that you can purchase, but the truth is that it’s not a thing. You can do many things to secure your application from threats, and some of those things don’t come in a single package. For example, if you want to ensure that your data is safe from hackers, you may need to install an SSL certificate on your website. You might also need to ensure that your website uses strong passwords and has two-step authentication enabled for users who try logging into it.
You can think about security as a lock on your front door—it’s not enough just to have a door with a lock; you also need to make sure no one can get through the door without having the right key (or combination). That’s what security is all about: protecting access points in your system while still allowing people access when they need it.
6. Developers aren’t properly trained in security
The first thing you need to know about Web application security is that you need training.
It’s not their fault!
Most developers are hired to write code, not secure code. And even if they were, there’s such a massive amount of information available that it’s hard for anyone to keep up with it.
But the truth is, when you don’t know what you’re doing, you leave yourself wide open to many potential problems. That can mean anything from simple mistakes like sending passwords over email instead of using HTTPS encryption or storing sensitive data in plain text files instead of encrypted databases (which we’ll talk about more later).
7. Developers still don’t understand cryptography
Cryptography is the science of encrypting information.
Cryptography is everywhere on the web: securing your credit card information when shopping online to protect your passwords from hackers trying to steal them. There are so many different types of encryption algorithms available today that it can be hard to keep up with them all! But don’t worry—we’ll give you a quick rundown in this post and then show how easy it is for developers like yourself to leverage these tools for your applications.
In software development, cryptography ensures the security and integrity of data within an application. The purpose of encryption is to make it impossible for someone who doesn’t have access to your system to read the content of a file or message, even if they have access to the hardware on which it was stored.
Unfortunately, cybersecurity experts say that many developers don’t fully comprehend how cryptography works and how important it is for protecting data. For example, most developers don’t understand a cryptographic hash function or how it can be used in web applications.
Security isn’t an afterthought — it’s part of the initial design.
Every developer knows that security is important. But, when you’re working on a deadline, the last thing you want to do is spend time re-designing for security.
But you should! That’s because it’s not just about adding in a few lines of code or checking in some new features—it’s about taking a step back and looking at your application. And when you do that, you might find that parts of your app need more protection than others.
For example: Maybe one part of your app handles sensitive user information, like credit card numbers or social security numbers. Or maybe another part has high-value assets like customer data and product configuration settings. These things need extra attention from a security standpoint, so take some time to consider them before moving forward with development and deployment.
8. Use encryption for data in transit and data at rest
When you send or store data, you should encrypt it. Encryption is a way of encoding information so that only authorized users can read or access it. There are two types of encryption: symmetric key encryption and public-key encryption.
Symmetric key encryption uses the same key to encrypt and decrypt data. It’s easy to use but relatively slow compared to public-key encryption.
Public-key encryption uses two keys — a public key and a private key — for encrypting and decrypting data. The public key encrypts data; the private key decrypts it.
9. Coding errors can lead to security issues
If you’re a developer, you know that coding errors are inevitable. They’re part of the process, and they’re unavoidable. But as much as we’d like to think otherwise, coding errors will still happen. The trick is to avoid them regarding your web application’s security features.
While it might seem like a good idea at first glance, developers will often try to patch over a vulnerability by adding new code to fix the problem in place of what was there before. Unfortunately, this is often not enough because the new code may not work as intended or might have been written incorrectly in the first place.
Instead, developers should focus on discovering why something happened first and then ensuring that their fix doesn’t introduce any new vulnerabilities—or at least doesn’t worsen existing ones.
10. Pinpoint the gaps with the OWASP Top 10 List
If you’re a developer, security is probably not the first thing that comes to mind when you think about web application development. But with the rise in data breaches and hacks, it’s time to take web app security seriously.
The OWASP Top 10 list is a great way to get started. It covers all of the most common security issues that developers encounter when building out their web applications. These include cross-site scripting (XSS), injection attacks, broken authentication and session management, insecure direct object references (IDOR), and deserialization.
If you’re just getting into this whole “security thing,” it can be hard to know where to begin—but it doesn’t have to be! The OWASP top 10 list can help pinpoint areas where your application could use extra love and attention regarding security.
In a nutshell
While web application security is a broad topic and, without any doubt, can fill volumes of books, there are some common best practices that you can employ to ensure the security of your web applications with minimum effort and required time. You do not need to be an expert or deeply understand the frameworks or libraries used. We are sure that all security experts will agree that focusing on a few core principles, complemented by automating tasks using secure coding practices and libraries or API, will reduce the attack surface of your web application significantly, which ultimately leads to a more secure, stable and robust application you can be proud of.
How Ateam Soft Solutions can help?
Web app security is a big deal. The internet is full of threats and attacks, and your web application must be secure to keep your users safe.
Ateam can help you with web app security. We can protect your clients from attacks by keeping them safe from malicious actors on the internet.
We offer various services and solutions to ensure your web application is secure and reliable. Our team of experts is highly skilled in web application security, and we take pride in our ability to provide you with the best possible results.
Our services include:
Application Penetration Testing:
We use various methods to test the security of your application, including manual testing, automated testing, and black box testing.
Web Application Firewall:
We install a firewall on your server that ensures all incoming traffic is legitimate before allowing it into your system. This helps prevent hackers from gaining access to your data.
Security Audits:
We conduct audits on your current systems to identify areas for improvement and come up with recommendations for new solutions that will increase your overall protection level against attacks from malicious sources outside the company itself (i.e., third-party vendors).

